Four Reasons Security Managers Should Deploy Counter-UAS Solutions
The Unmanned Aircraft Systems (UAS) industry is the most dynamic growth sector of the global aerospace industry. Since the United States' first operational use of armed UAS in 2001, rapid advances in the underlying technologies needed to manufacture drones, have allowed the devices to proliferate. Today, drones are widely implemented by both military and commercial customers, causing the market to swell from $4.4 billion in 2018 to an estimated $63.6 billion by 2025.
For security managers, drones pose an entirely novel threat, as the technology used in one application for infrastructure maintenance can be easily refitted to cripple any number of facility operations in another. This is why Counter UAS (C-UAS) devices have become an increasingly essential part of an end-to-end security solution. Built to detect, locate, identify, track, and then mitigate both ground-based and aerial threats, C-UAS perimeter intrusion detection systems (PIDS) layer industry-leading thermal sensors and radar devices to deliver robust, round-the-clock security capabilities for facilities of every kind, in any weather condition.
Below are four reasons why security managers should invest in Teledyne FLIR C-UAS solutions.
1: Preprogrammed Detection
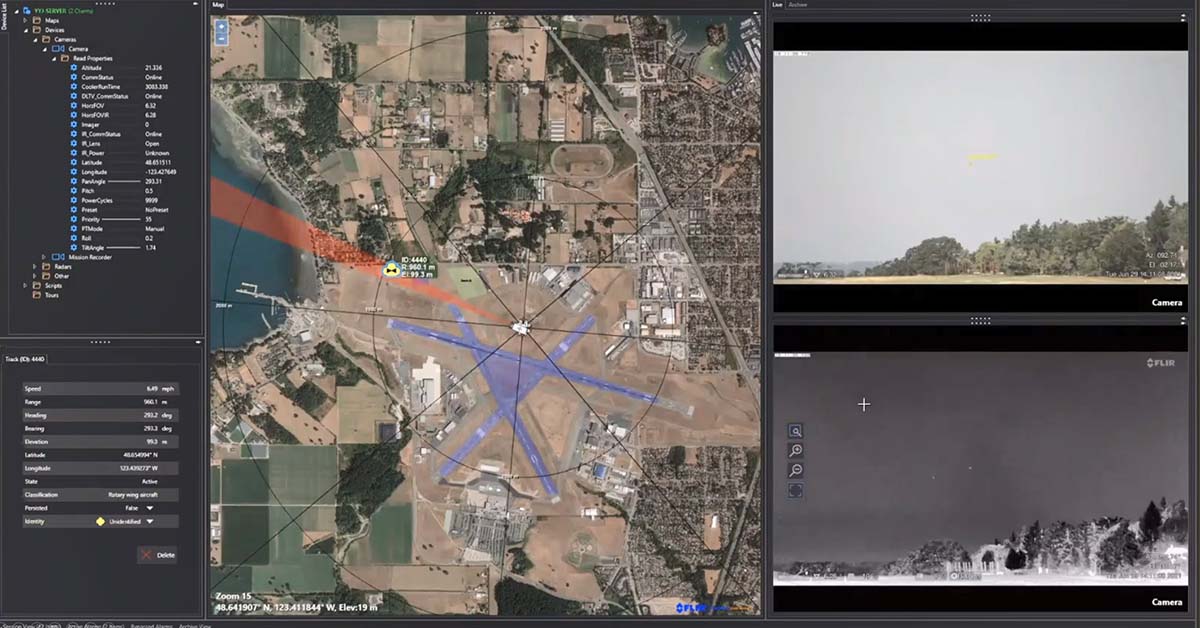
FLIR C-UAS solutions are optimized to detect any kind of intrusion in all weather conditions, day or night, delivering extended detection ranges and performance compared to other solutions. As part of FLIR’s C-UAS solution, long-range drone detection radars, such as the Ranger R20SS-3D or the R8SS-3D, are built to track multiple targets simultaneously, monitor predetermined coverage areas several times per second, and run 24/7, in order to protect perimeters from ground and aerial threats.
Because they operate in the X-band, i.e. a type of radar wave that falls between 8.0 GHz and 12 GHz, FLIR long-range drone detection radars are minimally affected by adverse weather or precipitation. They are also able to detect everything from preprogrammed or customized drones to parachutes, mylar balloons, and small aircraft. When integrated with other devices, such as industry-leading thermal sensors, these systems reduce infrastructure costs with very low maintenance and no recurrent fees, improving system ROI.
If an enemy drone were to approach a facility’s perimeter in the dead of night, even if there were a rainstorm, or heavy fog rolling in—a FLIR long-range detection radar would still be able to detect the presence of the drone and continue to geolocate the drone’s position, as it approached the perimeter, sending constant, real-time alerts to security personnel.
2: Multi-Sensor Identification
FLIR Ranger radars were designed to integrate with pan-tilt-zoom (PTZ), multi-sensor systems, such as the Ranger HDC MS, establishing multiple layers of detection and verification to deliver robust perimeter protection. By combining thermal and visible sensors with radar, for instance, EO/IR can verify any intrusion detection alert from a radar and visually confirm where and what a target is, using advanced video classification and tracking analytics. This not only reduces the cost of false alarms, but it also offers security personnel and first responders detailed intrusion detection data. When it comes to perimeter intrusion and crime prevention, the more situational awareness the better.

For example, say a long-range FLIR radar were to detect an incoming drone and provide geolocation data to paired PTZ cameras and the security operations team. On command, the multi-sensor PTZ would slew to the located threat, to identify and confirm that it is an enemy drone, delivering actionable data for first responders to use in their response.
In addition, complementary 3rd party RF systems can be integrated with the solution, to offer an additional layer of detection and classification with the radar back up to detect pre-programmed and customized drones that are “invisible” for these systems.
3: Dynamic Tracking
FLIR systems are also outfitted with tracking analytics, which become increasingly important as the drone flies closer to the perimeter. At long range, the drone’s location can be sent from the radar to the camera to maintain visual confirmation of the threat. As the drone gets closer, it becomes increasingly important that the tracking feedback loop is highly responsive to changes in flight path, so tracking based on the image is a more accurate method. This auto-tracking feature allows security operators to stay focused on coordinating the response to a drone threat, rather than worrying about keeping the camera pointed at the drone.
4: Seamless Mitigation
FLIR partners with several third-party effector tools that are purposely built to jam and spoof incoming enemy drones. Jamming will disrupt the radio frequency (RF) and satellite communication links, such as GPS, GLONASS, etc., making enemy drones inoperable, whereas spoofing technologies can take control of enemy UAS systems by broadcasting false GPS signals to the UAS’s receiver. Laser/microwave devices are also used to direct energy beams to damage or destroy UAS airframes.
Often, detecting, identifying, and tracking isn’t enough—mitigation procedures are necessary for protecting critical assets. These multi-sensor C-UAS strategies, combining thermal sensors, ground-based radar, and effector tools not only keep enemy drones from breaching the perimeter, they also ensure those drones won’t be able to communicate any of its own real-time data back to remote operators. Every step along the FLIR C-UAS Kill Chain is critical for optimizing end-to-end PIDS performance.
At the end of the day, security personnel need to be agile, as perimeter threats no longer exclusively come from the ground. Protecting assets from air-based threats, such as UAS, drones, and small aircraft, is simply a must. The FLIR C-UAS response, including preprogrammed detection, multi-sensor identification, dynamic tracking, and seamless mitigation ensures every perimeter is secure—from every kind of threat, in any condition, 24/7.
